HTTP Firewall

HTTP Firewall
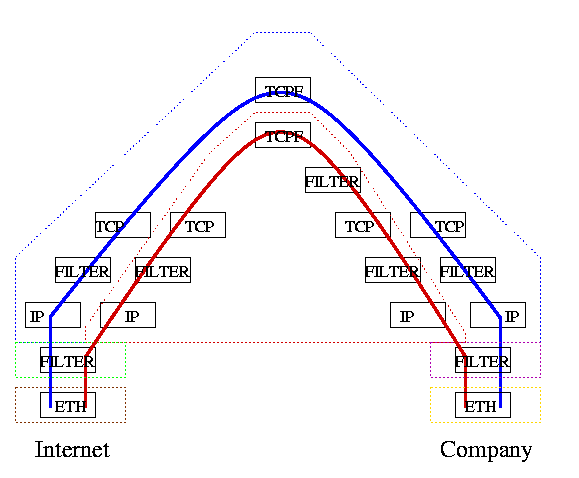
Our HTTP firewall is similar to a regular firewall, except it is specialized for HTTP traffic. Its goal is to limit the access of traffic to/from a protected network, and to limit the data flows within the firewall itself. Our example HTTP firewall assumes that there are two levels of trust: (1) external users that access the Web server on the protected network of a company, and (2) company users that access the protected network from an enclave of the same company. These two data flows are separated in the firewall.
The router graph shows not only the routers of the HTTP firewall, but it also shows the protection domains that contain the multi-instantiated routers. The blue protection domain processes the HTTP traffic of company users and the red protection domain processes external HTTP traffic. The blue and red lines show instances of paths created by company users and external users. The FILTER routers limit information flow on the respective path.
[Spat98a] Oliver Spatscheck, Jørgen S. Hansen, John H. Hartman and Larry L. Peterson. Optimizing TCP Forwarder Performance. Technical Report TR98-01, Department of Computer Science, University of Arizona (February 1998).
[Spat97] Oliver Spatscheck and Larry Peterson. Escort: A Path-Based OS Security Architecture. Technical Report TR97-17, Department of Computer Science, University of Arizona (November 1997).